Swim Fast.
Dive Deep.
Thrive Securely in the Cloud

OUR CUSTOMERS
Fast Time to Value. Proven Cloud Security at Scale.
At Orca Security, we’re trusted by customers around the world to secure their multi-cloud environments at scale. See and hear their stories directly about how they’ve transformed their cloud security strategy.
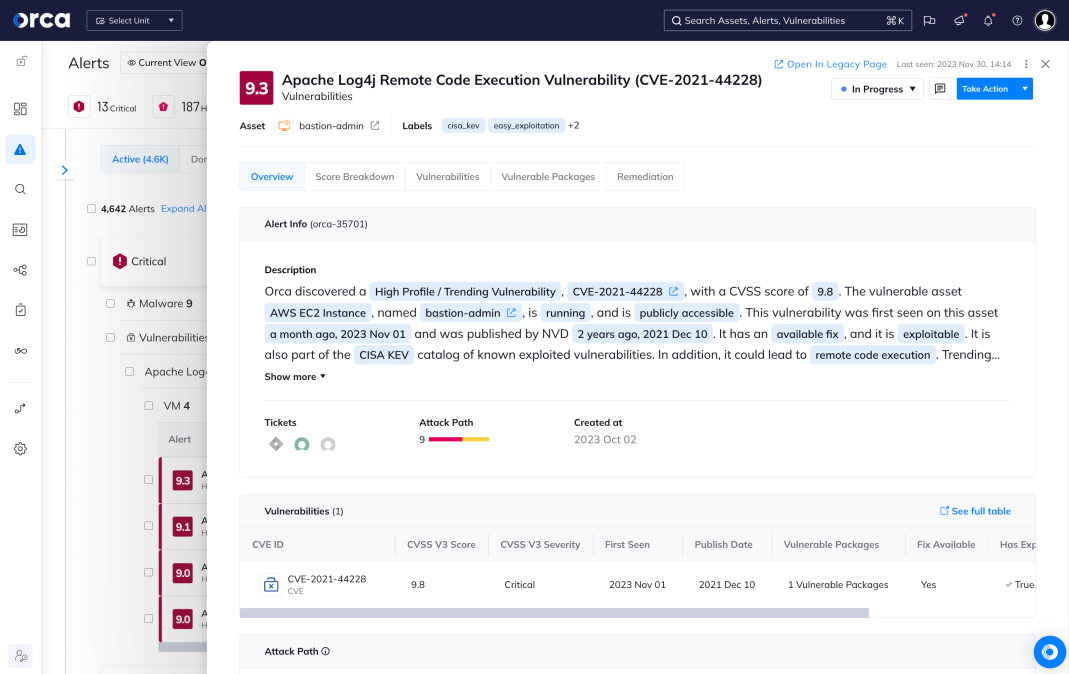
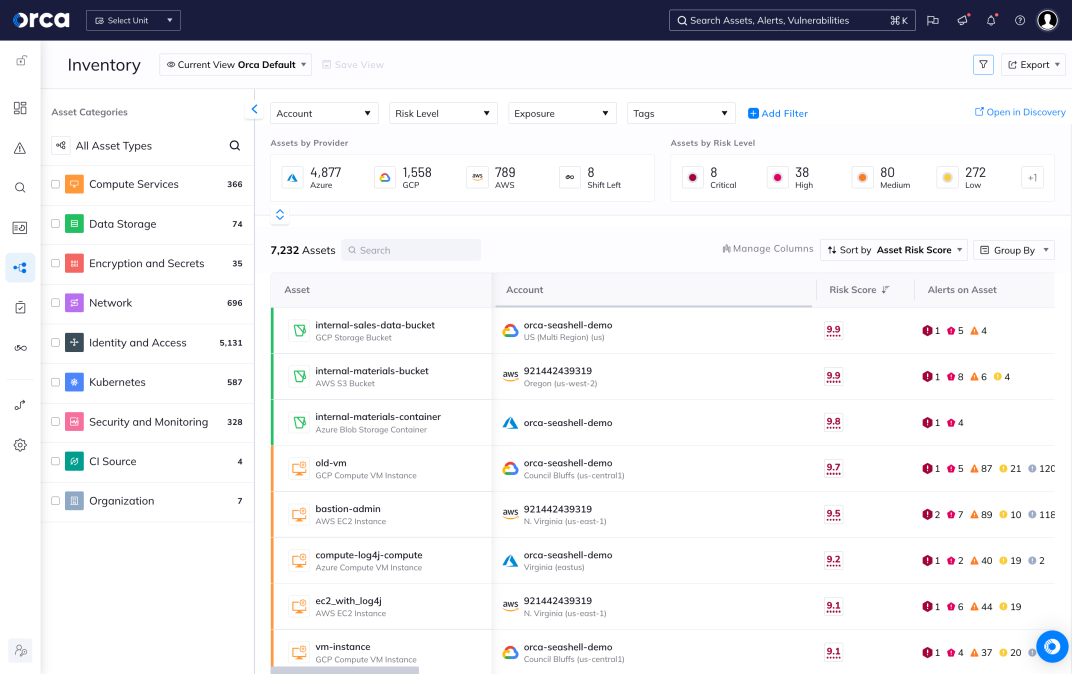
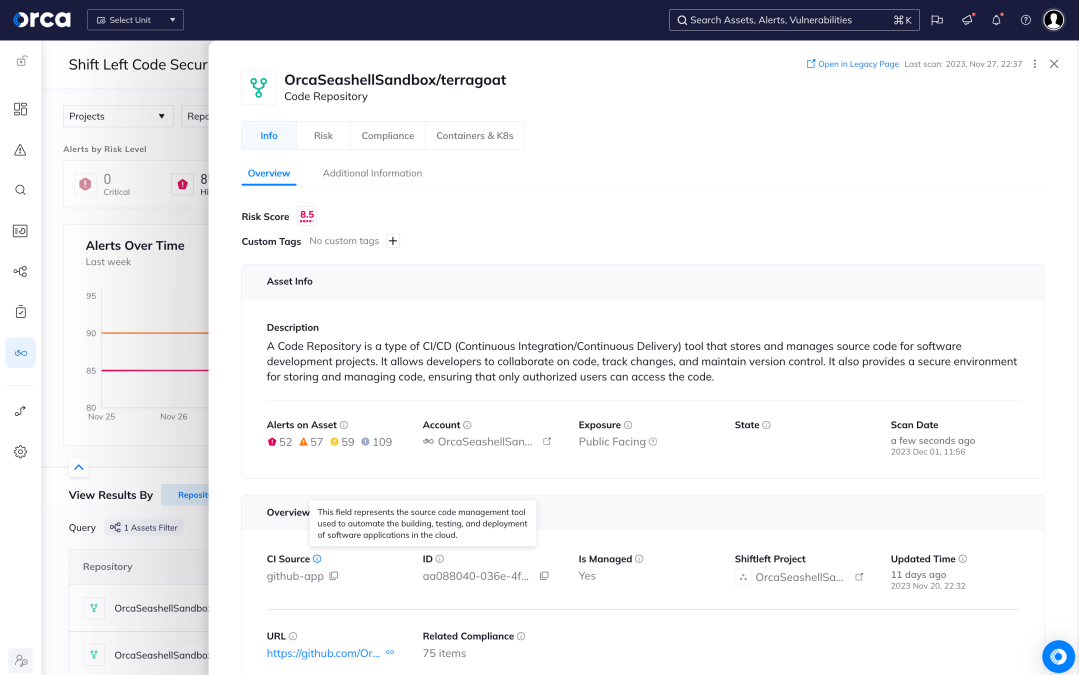
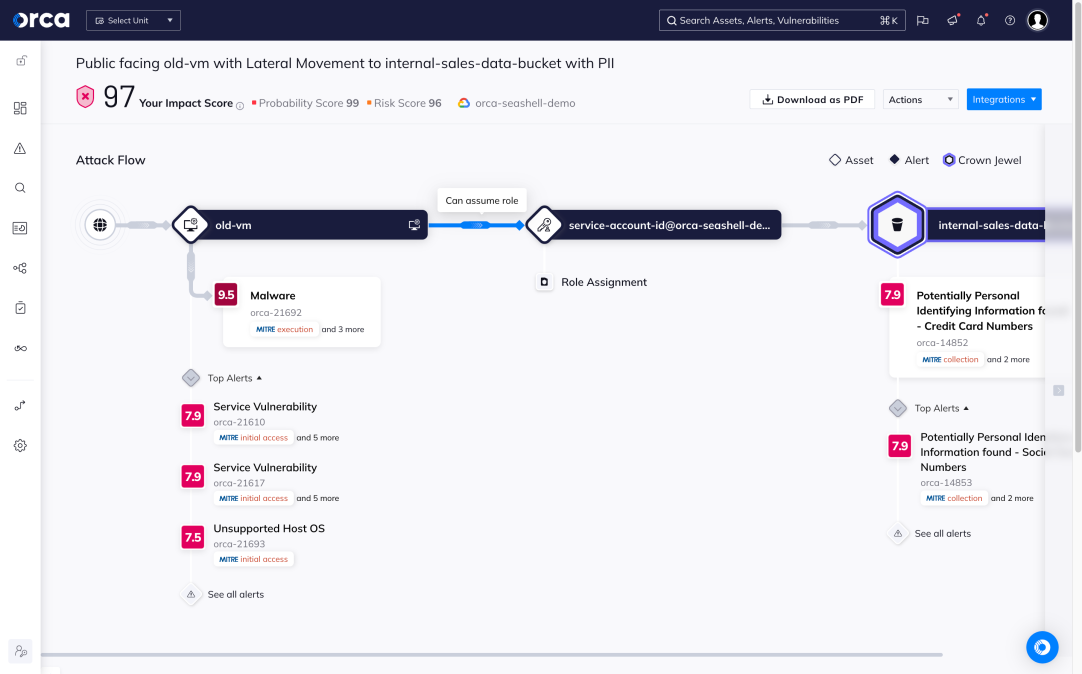
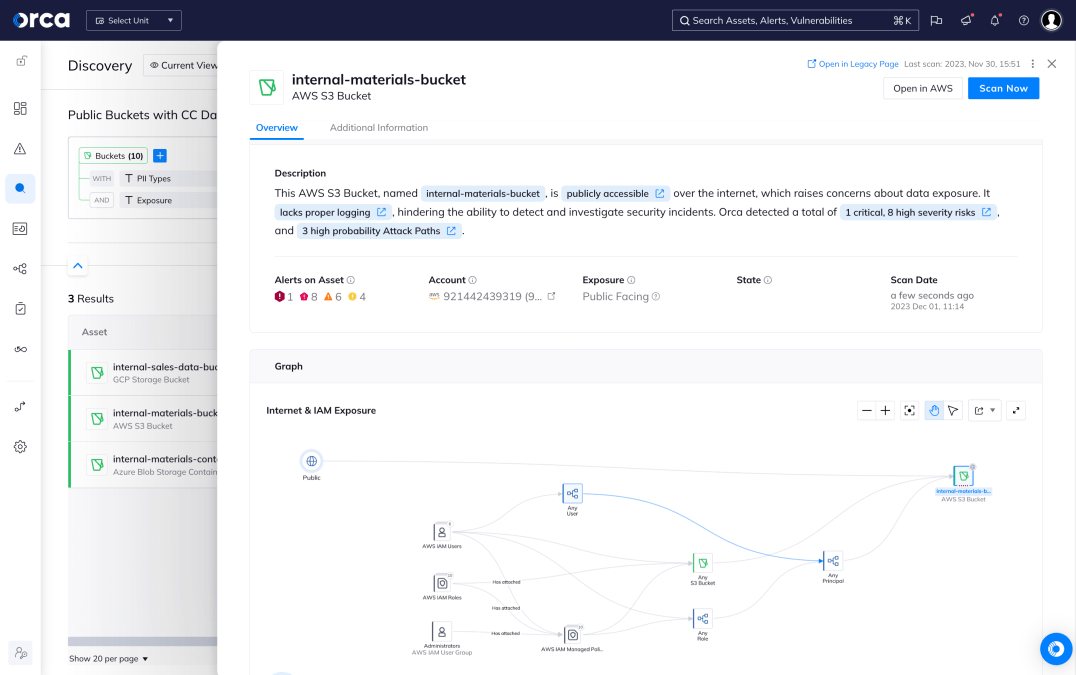
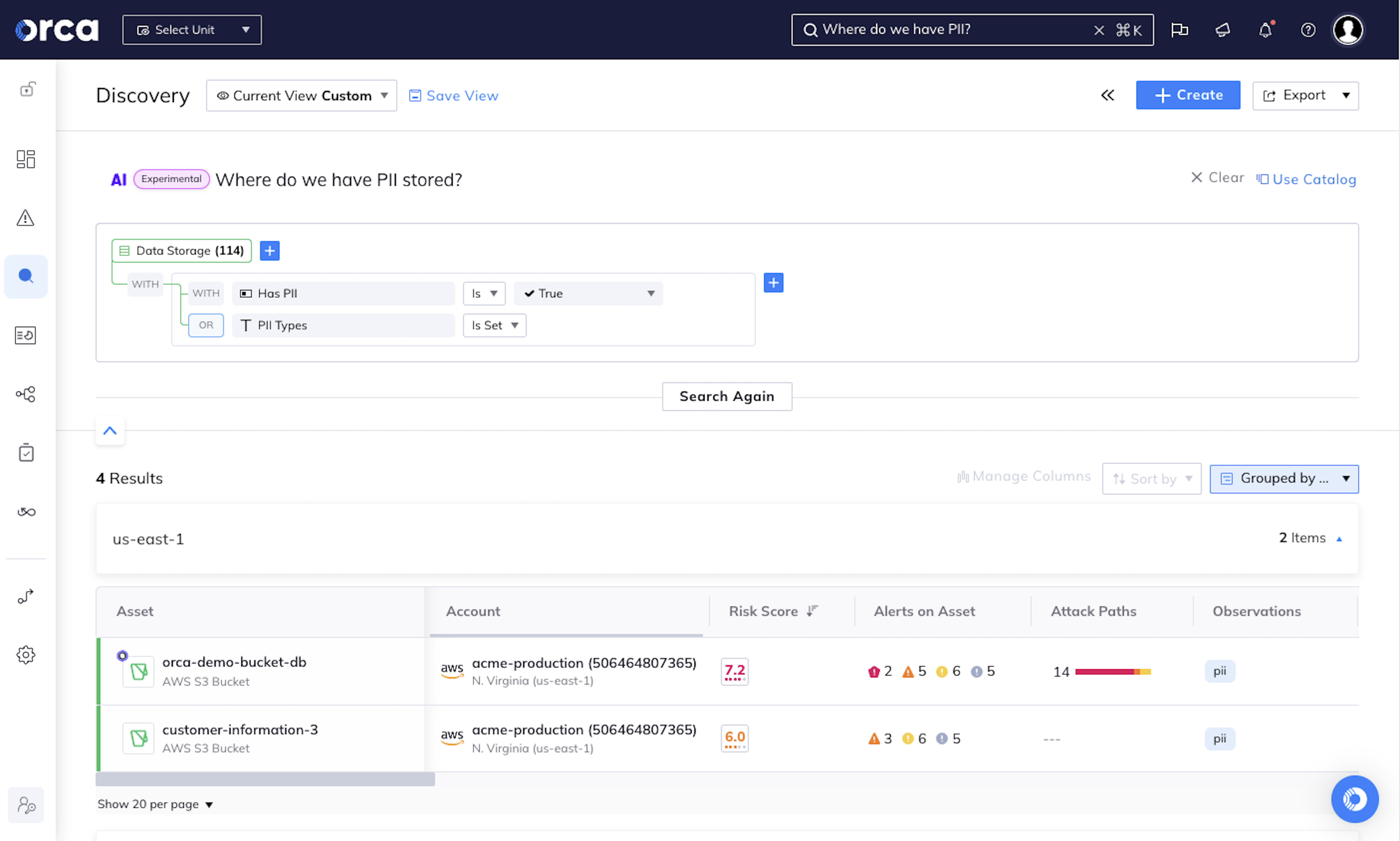
Understand and prioritize your greatest cloud risks
The Orca Cloud Security Platform easily connects to your cloud environment to deliver complete coverage across all cloud risks – spanning misconfigurations, vulnerabilities, identity risks, data security, API exposure, and advanced threats:
- Stop sifting through long lists of alerts and prioritize the top combination of risks that matter
- Automatically identify PII and crown jewel assets to prevent critical risks to your business
- Quickly understand contextual risk across multi-cloud environments
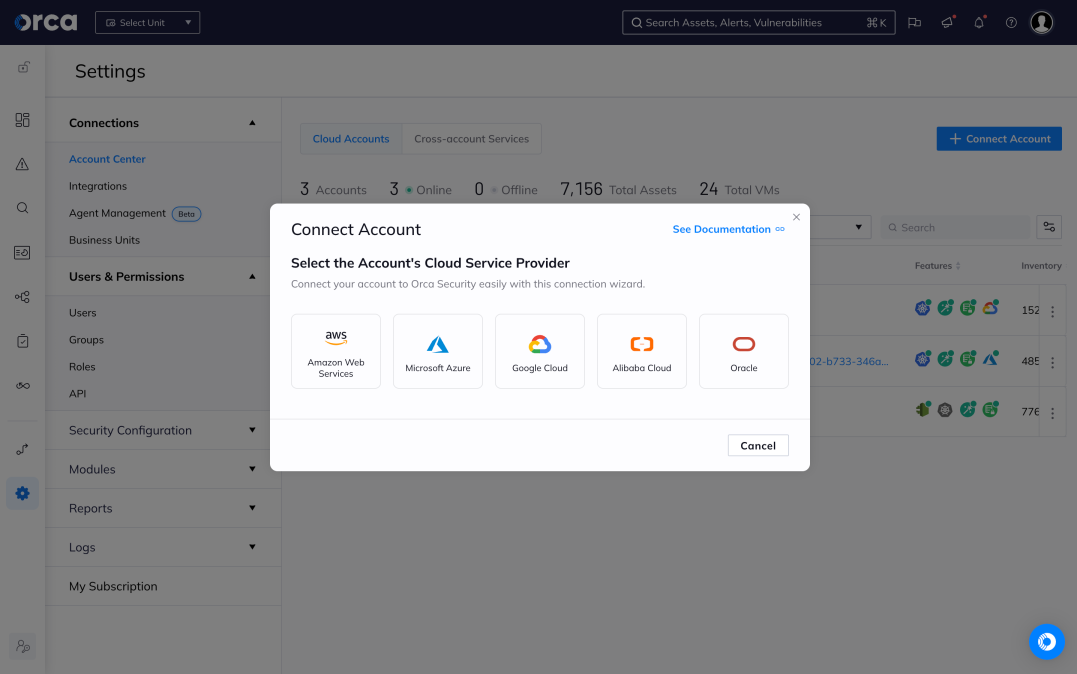
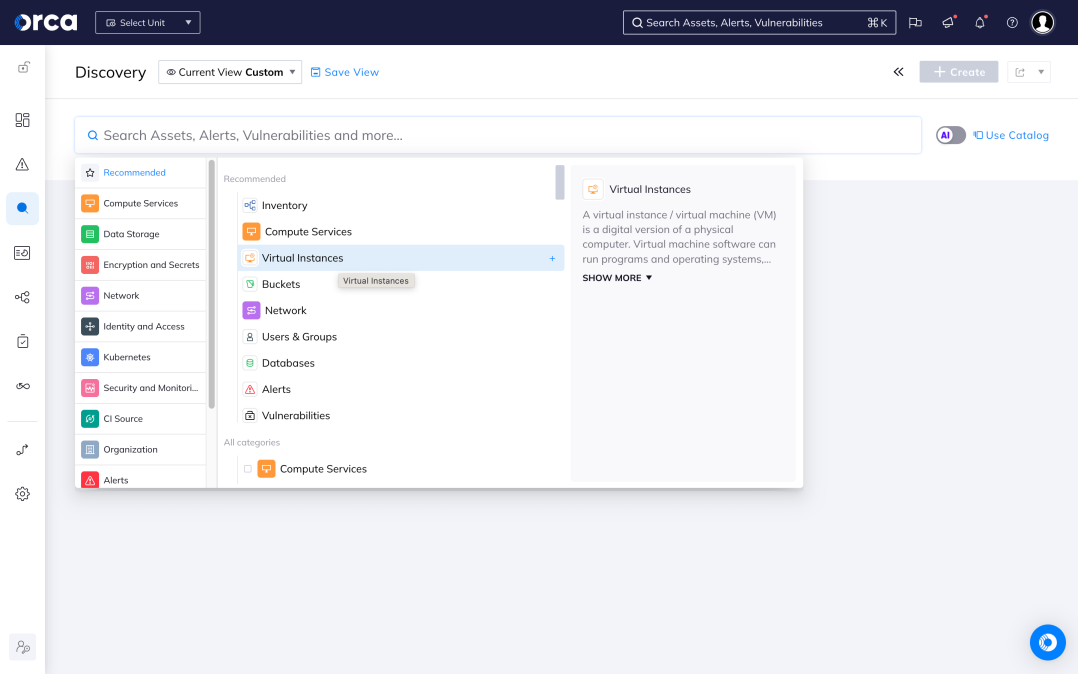
Unify cloud security in a single platform
Orca brings together core cloud security capabilities, including vulnerability management, multi-cloud compliance and posture management, cloud workload protection, container security, and more in a single, purpose-built solution.
- Enable faster, more effective security outcomes without the need to continually onboard and implement multiple, siloed security tools
- Easily activate advanced capabilities, such as API Security, Cloud Detection and Response, and Shift Left Security, to address more cloud security challenges and increase visibility
- Gain unmatched context into your cloud environments to prioritize risks across the entire tech stack
New
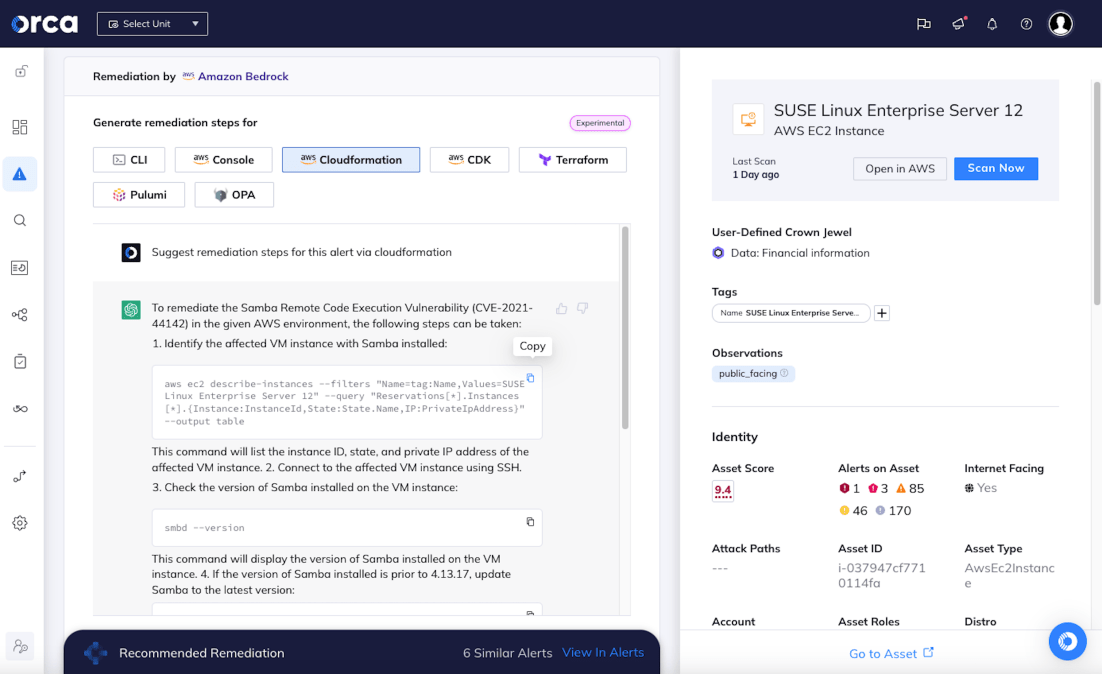
Powered by AI to augment cloud security
Orca is at the forefront of leveraging Generative AI to supercharge cloud security by lowering skill thresholds, simplifying tasks, accelerating remediation, and improving understanding of the cloud environment.
Working together to secure your cloud
Orca Security empowers technology partners and service providers to deliver the most comprehensive coverage and visibility of all risks across the cloud.

Explore Orca Cloud Security Solutions
Cloud Security Posture Management
Continuously monitor, Identify and remediate misconfigurations across clouds, including cloud infrastructure posture management, automated remediation, pre-deployment IaC scanning, and reporting.
Cloud Workload Protection
Protect cloud VMs, containers and Kubernetes applications, and serverless functions across clouds. Prioritize risks and compliance issues, manage workload and application vulnerabilities, identify malware, and integrate security across the full application lifecycle.
Cloud Infrastructure Entitlement Management
Detect identity misconfigurations, ensure least-privilege compliance and access, and monitor identity hygiene metrics. Integrated with leading SSO and IDP tools.
Multi-Cloud Compliance
Achieve regulatory compliance with over 100 out-of-the-box frameworks, CIS Benchmarks, and custom checks across multiple cloud platforms–instantly covering 100% of your cloud estate to address compliance gaps strategically.
Vulnerability and Patch Management
Manage vulnerabilities and prioritize risks. Understand operating system, package, and other vulnerability issues across Linux and Windows VMs, container images, and serverless functions.
Shift Left Security
Scan Infrastructure as Code (IaC) templates and container images from a single platform, ensuring that any vulnerabilities, secrets, misconfigurations, and malware are detected early in the development process.
Award-Winning Cloud Security Company
2023 GigaOm Radar for CSPM
Orca Security is recognized by GigaOm as a Leader and Outperformer for CSPM.
Global AWS Security Partner of the Year
Orca Security is proud to be the 2022 AWS Security Partner of the Year.